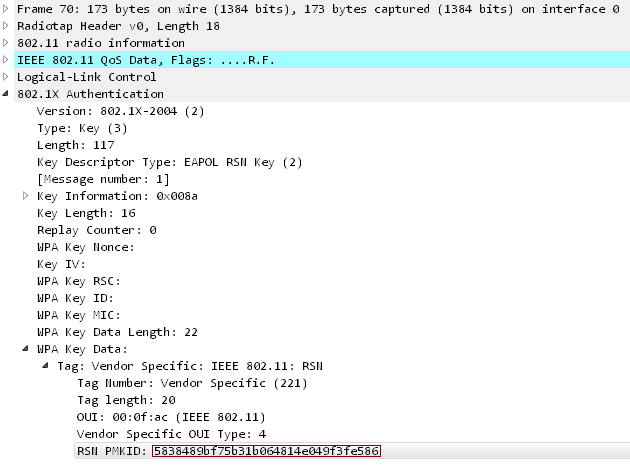
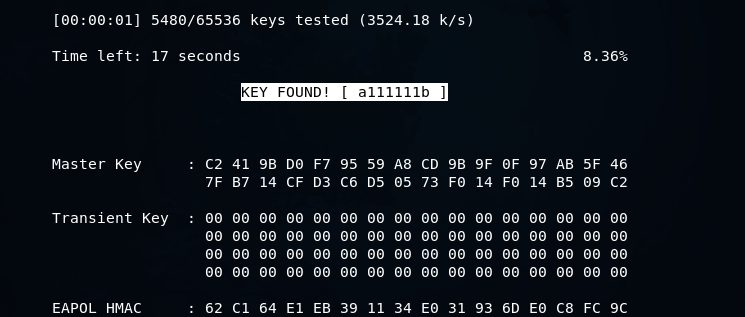
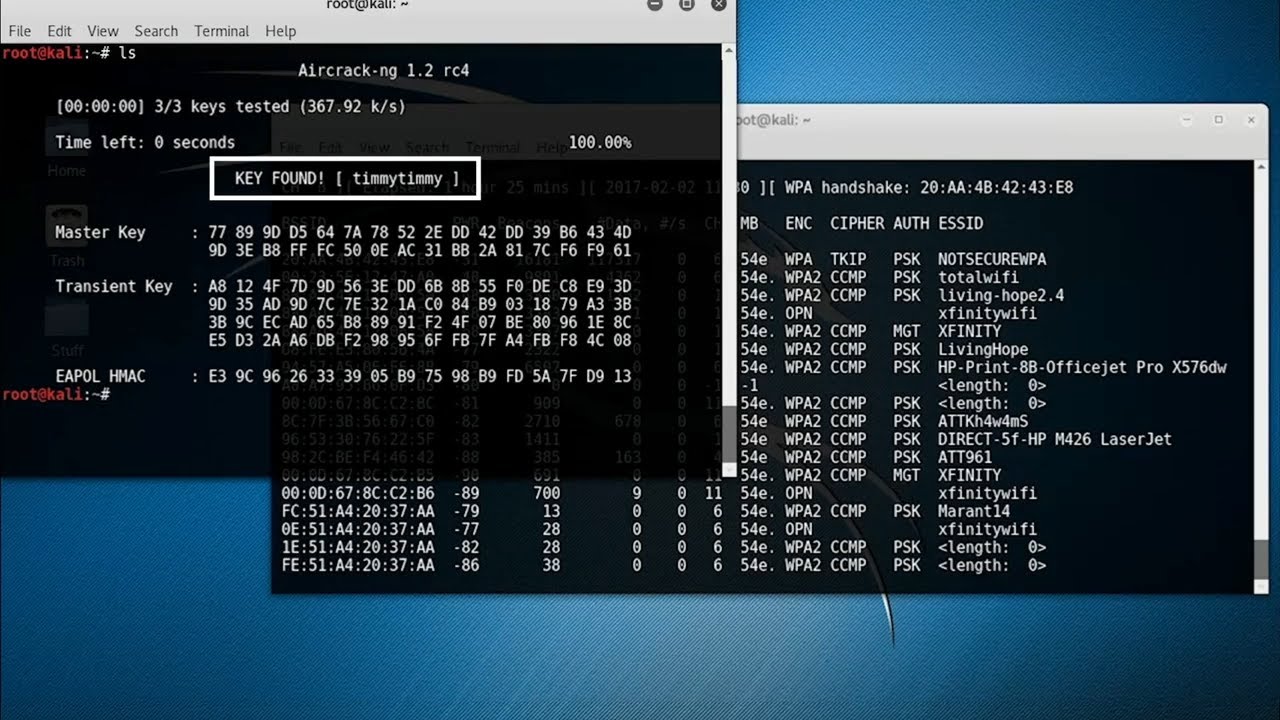
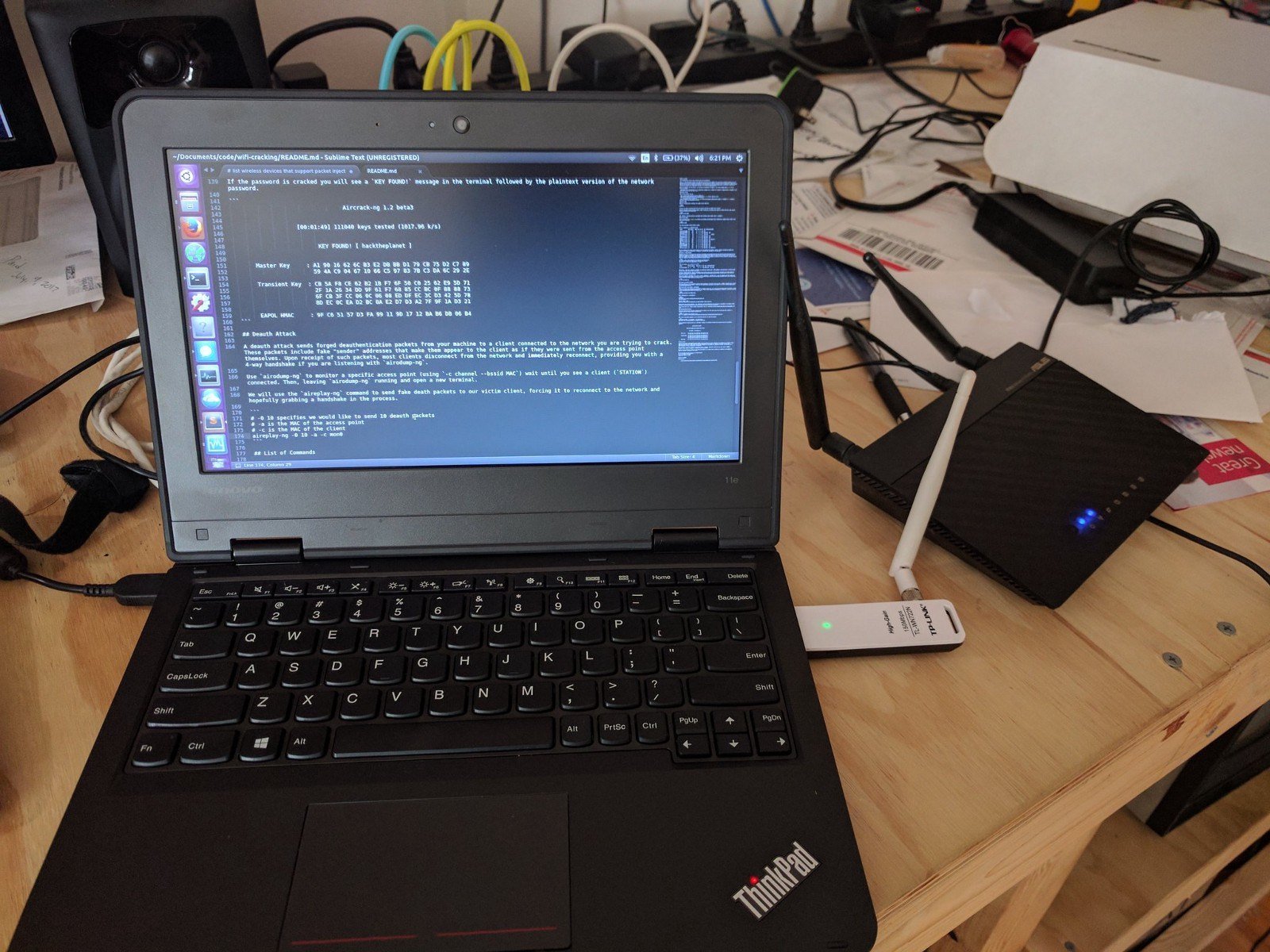
GitHub - jeanphorn/wordlist: Collection of some common wordlists such as RDP password, user name list, ssh password wordlist for brute force. IP Cameras Default Passwords.

Hello Friends Today I Am Going to Show You How To Hack Wifi Without Using Wordlist Or You Can Call it as Hacking Wifi Password Using R... | Wifi hack, Wifi, Wpa


![Hashcat tutorial for beginners [updated 2021] | Infosec Resources Hashcat tutorial for beginners [updated 2021] | Infosec Resources](https://resources.infosecinstitute.com/wp-content/uploads/2018/04/122120-2.png)

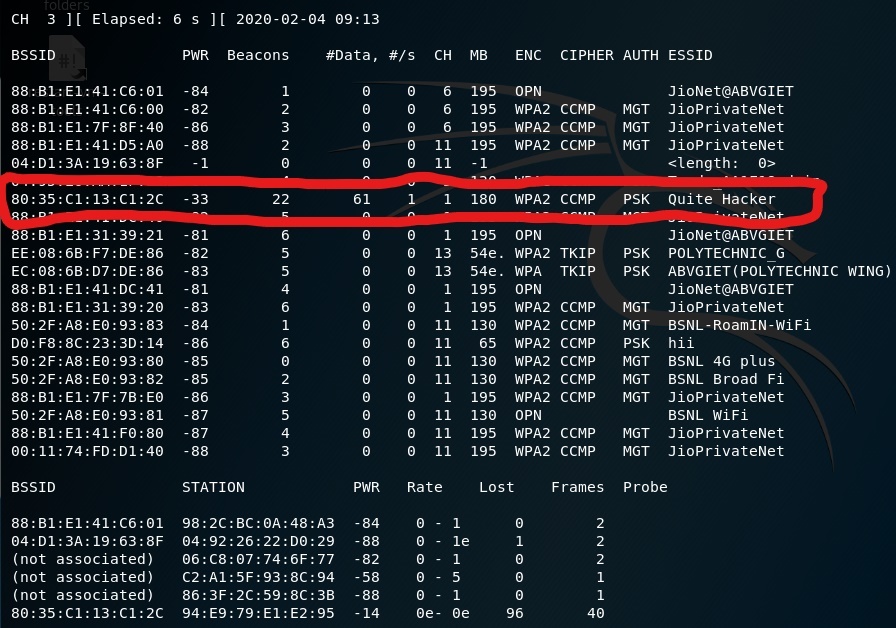
![Hashcat tutorial for beginners [updated 2021] | Infosec Resources Hashcat tutorial for beginners [updated 2021] | Infosec Resources](https://resources.infosecinstitute.com/wp-content/uploads/2018/04/122120-4.png)
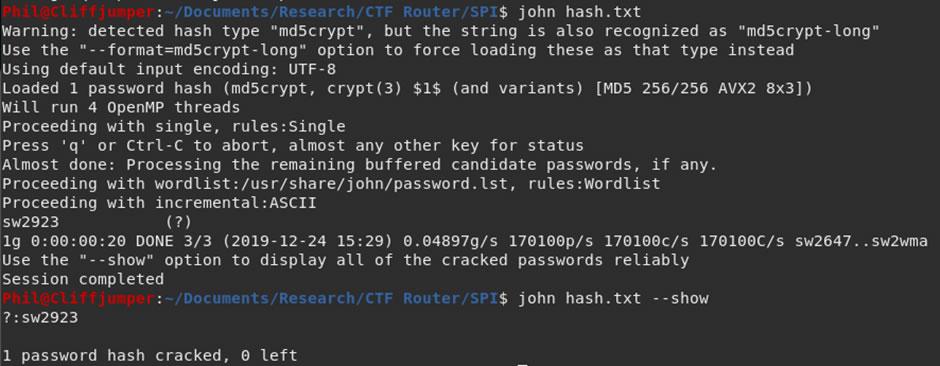
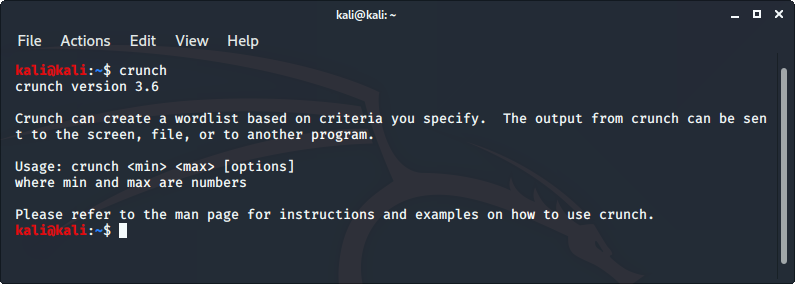



![Cracking Cisco login using custom wordlist - Kali Linux Intrusion and Exploitation Cookbook [Book] Cracking Cisco login using custom wordlist - Kali Linux Intrusion and Exploitation Cookbook [Book]](https://www.oreilly.com/library/view/kali-linux-intrusion/9781783982165/graphics/image_04_032.jpg)



![Hack WPA & WPA2 Wi-Fi Passwords with a Pixie-Dust Attack using Airgeddon [Tutorial] - YouTube Hack WPA & WPA2 Wi-Fi Passwords with a Pixie-Dust Attack using Airgeddon [Tutorial] - YouTube](https://i.ytimg.com/vi/SY0WMHTCCOM/maxresdefault.jpg)